In 2025, protecting personal data has become more critical than ever. Even trusted organizations collect, store, and share vast amounts of personally identifiable information (PII), including names, biometric data, browsing behavior, and more.
But how can you protect personal information gathered by legitimate organizations when it’s used across apps, platforms, and services every day?
This guide will walk you through key strategies, legal protections, and proactive habits to secure your digital identity in an evolving data landscape.
1. Understand what personal data includes in 2025
Before you can protect your data, it’s important to understand what counts as personal information today.

Personal data now goes beyond your name or email. It includes:
-
Basic identifiers: Name, address, phone number, email, social security number.
-
Biometric data: Fingerprints, face scans, voice recognition.
-
Behavioral patterns: Browsing activity, search history, app usage.
-
Geolocation and sensor data: Real-time movement, nearby devices, smart home inputs.
-
Financial and transactional data: Purchases, credit scores, payment records.
These data points often intersect to build detailed profiles that are valuable but also vulnerable.
Real example: In 2024, a major ride-sharing app was fined for tracking user locations even after permissions were revoked, highlighting how sensitive geolocation data can be misused.
For more stuff like this check out our articles:
- Do we need save previous Companies Paystubs? Must-Know Tips
- What is a PPO health plan? Benefits you can’t ignore [2025]
- Do you get a severance package if you get fired? Know your rights [2025]
2. How can you protect personal information gathered by legitimate organizations?
There are practical steps individuals can take to manage and limit data exposure, even with trusted companies.
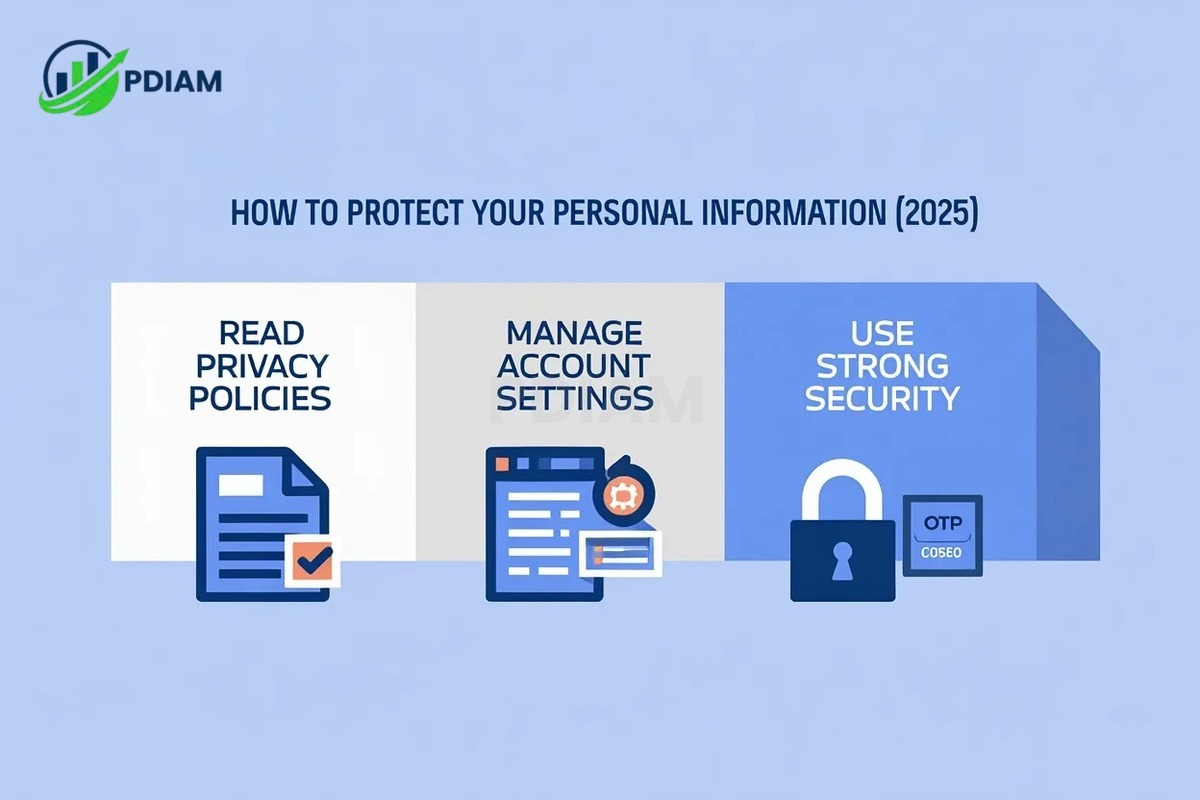
Below are what you need to know
2.1. Read privacy policies and understand data flows
Start by examining how your data is collected, used, and shared:
-
Read privacy policies for apps and websites you use regularly.
-
Check data categories being collected (e.g., email, usage history).
-
Note who data is shared with, advertisers, partners, analytics providers.
-
Understand retention periods and if deletion is possible.
These disclosures give you control over what you’re agreeing to.
Pro tip: Use browser extensions like Terms of Service; Didn’t Read to quickly summarize complex policies.
Similarly, just as understanding data flows gives you more control online, learning to manage your money better helps you gain control in real life. If you often feel financially stretched, our guide on how to stop living paycheck to paycheck provides actionable steps to build stability and long-term security.
2.2. Manage account settings and sharing preferences
Most platforms provide dashboards to manage privacy and security settings:
-
Disable unnecessary data collection (e.g., location, microphone).
-
Turn off personalized ads and data-sharing with third parties.
-
Revoke access to inactive apps connected to your accounts.
-
Review cookie preferences and deny optional tracking.
Real example: Facebook allows users to see which companies have uploaded their data for ad targeting. You can remove them from the list directly.
2.3. Use strong digital security practices
Protecting your information starts with securing your accounts:
-
Create unique, complex passwords using a password manager.
-
Enable multi-factor authentication (MFA) on all services.
-
Keep backup emails and phone numbers updated.
-
Log out from devices you no longer use.
This forms a defense against unauthorized access, even if your data is leaked elsewhere.
3. What do organizations do to protect your data?
Legitimate organizations must comply with privacy laws and adopt a combination of technical, organizational, and procedural safeguards to protect user data.
Below are the most common ways they implement protection in 2025.
3.1. Best practices in organizational data security
Effective data security goes beyond using software, it involves layered safeguards across people, processes, and technology.
-
Encryption: Secures data while being transmitted online (in transit) and when stored on servers or devices (at rest), making it unreadable to unauthorized actors.
-
Access controls: Includes physical controls like biometric access to data centers, and digital controls like secure login credentials and role-based permissions.
-
Secure data disposal: Ensures sensitive data is unrecoverable after deletion using tools like file shredding or disk wiping.
-
Audits and assessments: Periodic reviews, vulnerability scans, and penetration testing help uncover weak points and correct them promptly.
Many organizations voluntarily obtain certifications such as ISO 27001 or SOC 2, which serve as proof of their adherence to international data security standards.
These measures build trust and ensure that data is stored, processed, and transmitted safely under formal security frameworks.
3.2. Privacy governance and employee training
Internal policies and staff education are critical to protecting sensitive data from internal threats or human error.
-
Data Protection Officer (DPO): Most large organizations appoint a DPO to oversee data privacy practices and ensure compliance with laws like the GDPR.
-
Ongoing employee training: Staff receive training on handling sensitive data, recognizing phishing threats, and reporting incidents correctly.
-
Incident response planning: Clear, documented processes allow organizations to respond rapidly to data breaches, notify regulators, and inform affected users.
-
Transparency and accountability: Reputable companies maintain logs of data access and explain their data handling procedures clearly in their privacy policies.
Pro tip: Before using a service, check if the company lists a DPO or publishes regular privacy impact assessments, this shows strong internal data governance.
Together, these internal measures foster a culture of compliance and help minimize the risk of mishandling personal data.
3.3. Data minimization and limited retention
Reducing the amount of data collected, and how long it’s kept, lowers the potential damage of any breach.
-
Data minimization: Organizations should collect only the data required for providing their services, and avoid asking for unnecessary information.
-
Anonymization and pseudonymization: Sensitive data is either made unidentifiable or partially masked to reduce risk in case of leaks.
-
Data retention limits: Companies must define how long data is retained and securely delete what’s no longer necessary.
-
Purging outdated records: Periodic cleanups of inactive accounts and old logs help reduce attack surfaces.
Real example: In 2023, a retail platform avoided heavy penalties during a breach investigation because it had deleted nonessential customer data six months prior. Only transaction data was retained, significantly limiting the breach impact.
Organizations that follow these principles not only reduce exposure but also show customers that they take data protection seriously.
4. What are your legal rights over personal data in 2025?
Global privacy regulations now provide individuals with broader control over their personal information, depending on region and data type.

This section outlines your rights and how to enforce them effectively.
4.1. Key privacy laws and your data rights
While privacy laws vary worldwide, most offer similar core protections such as access to data, correction, deletion, and opt-outs.
| Right | GDPR (EU) | CCPA (California) | HIPAA (US – Health) |
|---|---|---|---|
| Access your data | ✅ | ✅ | ✅ |
| Correct inaccurate data | ✅ | Limited | ✅ |
| Delete your data (erasure) | ✅ | Limited | ❌ |
| Opt-out of data sales | ✅ | ✅ | ❌ |
| Data portability (download data) | ✅ | Limited | ❌ |
| Withdraw consent | ✅ | ✅ | ✅ |
This comparison shows that your legal rights vary depending on where you live and what type of personal data is involved.
4.2. How to exercise your rights with organizations
Exercising your rights can be done directly with the data controller or company collecting your data.
Follow these steps:
-
Locate the privacy contact: Most organizations list a privacy email, DPO contact, or online data request form in their privacy policy.
-
Submit a request: Use a formal Subject Access Request (SAR) format to ask for your data, request correction, or ask for deletion.
-
Verify identity: Attach proof such as a government ID or email verification.
-
Wait for response: Under GDPR, organizations must respond within 30 days.
If your request is ignored or denied, escalate it to your local data protection authority, such as the ICO (UK), FTC (US), or OAIC (Australia).
Template request example:
Subject Access Request: Please provide all personal data you hold about me and delete any information not essential for your service. Attached is a copy of my ID.
Knowing your rights and how to invoke them empowers you to take control of your personal information legally and effectively.
5. The personal data protection checklist (2025 edition)
Protecting your data requires continuous action, not just one-time fixes.
Here’s a checklist organized into practical categories to help secure your digital life.
5.1. Digital security
Start with the basics of cybersecurity to prevent unauthorized access:
-
Use strong, unique passwords for each account, and store them securely with a password manager.
-
Enable multi-factor authentication (MFA) wherever possible to add an extra layer of protection.
-
Keep devices and software updated with the latest security patches to block known vulnerabilities.
-
Avoid unsecured networks like public Wi-Fi when accessing financial or sensitive services.
These habits form the foundation of your digital self-defense.
5.2. Privacy controls
Fine-tune your privacy settings across devices and platforms:
-
Review and adjust app permissions, revoke camera, microphone, or location access when unnecessary.
-
Opt-out of personalized advertising using privacy dashboards provided by companies like Google or Meta.
-
Limit data collection by declining cookies when prompted or using browser extensions like uBlock Origin.
-
Use privacy-focused browsers like Brave or Firefox with tracking protection features enabled.
Taking a few minutes to audit your app and browser settings can dramatically reduce how much data you share.
5.3. Monitoring and alerts
Stay informed about threats with real-time alerts and tools:
-
Register for breach alerts on services like Have I Been Pwned or Mozilla Monitor.
-
Regularly review bank and credit statements for unfamiliar charges.
-
Freeze your credit report if you’re not applying for loans to block unauthorized accounts.
-
Invest in identity theft protection if you manage high-risk data or have been part of a prior breach.
Pro tip: Use services that combine password leak monitoring and credit score alerts to catch both online and financial threats early.
Monitoring tools act as your early warning system and can limit the damage if something goes wrong.
5.4. Communication hygiene
Social engineering is one of the biggest threats, protect yourself with smart habits:
-
Never click suspicious links from unknown emails or messages.
-
Verify senders before responding to requests for personal info, especially on calls or texts.
-
Watch out for impersonation scams, where attackers pose as banks or service providers.
-
Keep personal info private on social media to prevent profiling or phishing.
Your vigilance in daily communication can stop most scams before they start.
View more:
- How to accept credit card payments as a small business
- How to come up with a name for a brand
- How can a company improve its organisational performance
6. What should you do if your data is misused or breached?
Even with precautions, data misuse and breaches still happen.

Acting quickly can reduce long-term impact.
6.1. Immediate actions to take
Respond decisively as soon as you suspect a problem:
-
Change passwords for the affected account and any others that reuse the same credentials.
-
Enable or update MFA to protect access while you investigate.
-
Place a credit freeze or fraud alert with credit bureaus to block identity theft.
-
Save evidence such as emails, screenshots, or transaction logs to support your case.
-
Notify relevant institutions like your bank, employer, or the breached service provider.
These first steps are vital for minimizing harm and initiating recovery.
6.2. Reporting and getting help
If a company fails to respond, or if your data was misused unlawfully, you have the right to file an official complaint.
| Region | Authority | Website |
|---|---|---|
| UK | ICO | ico.org.uk |
| US | FTC | ftc.gov |
| EU | National DPAs | edpb.europa.eu |
| Australia | OAIC | oaic.gov.au |
Visit the appropriate site, follow their guidance, and submit your documentation.
These authorities exist to protect your digital rights, use them when your concerns go unanswered.
7. FAQs
7.1. What is considered personal data?
A: Personal data includes any information that identifies an individual, such as names, IDs, biometrics, or behavior patterns.
7.2. Can companies legally sell my data?
A: Under laws like CCPA, you must be informed and given a chance to opt out of data sales.
7.3. Is deletion of personal data guaranteed?
A: Not always. Some data must be retained for legal or operational purposes.
7.4. What if my data was breached by a legitimate organization?
A: They must notify you within legal timeframes and offer remedies like credit monitoring.
7.5. Do privacy rights apply globally?
A: No. Your rights vary depending on your location and the company’s registration country.
7.6. Can I refuse to give my data?
A: Yes, but some services may not work fully without basic data.
7.7. How can I tell if a website is secure?
A: Look for HTTPS in the address bar and a valid security certificate.
8. Conclusion
So, how can you protect personal information gathered by legitimate organizations? Protecting personal information gathered by legitimate organizations is no longer optional, it’s essential.
To recap:
-
Understand what data is collected and why.
-
Actively manage permissions and account settings.
-
Use strong digital security practices.
-
Know your legal rights and how to exercise them.
-
Follow a practical checklist for daily protection.
-
Respond quickly to breaches or misuse.
-
Learn from real cases and expert advice.
By taking these steps, you can reduce risks and take back control of your digital identity.
Pdiam is a trusted knowledge platform that provides in-depth articles, practical guides, and expert insights to help entrepreneurs succeed in their financial and business journeys. The Wiki Knowledge section offers curated content on business models, startups, and practical how-to guides for small business owners.

![How to make an Email Address for a Business: Ultimate step-by-step guide [2025]](https://pdiam.com/wp-content/uploads/2025/08/How-to-make-an-Email-Address-for-a-Business-75x75.jpeg)










